Partner with confidence using a risk-based approach to third-party due diligence
Protect your company’s reputation and compliance standing with a credible and defensible third-party program that anticipates potential threats.
Effectively screen & monitor new partners
Save time and see deeper with our proprietary data-and-AI-driven monitoring systems. Ensure transparency and mitigate hidden risks with Diligent's ultimate beneficial ownership search.
Streamline the third-party lifecycle
Drive efficiency with customizable workflows, automated renewals, streamlined approvals, and compatibility with external systems.
Power your ABAC program with deep insight
Leverage out-of-the-box interactive analytics and reporting to track the health of your third-party program. Use meaningful insights to respond proactively to trends instead of chasing them.
Take due diligence to the next level
Go beyond one-size-fits-all due diligence and adopt a risk-based approach backed by AI-driven database screening, human research and in-depth field investigations.
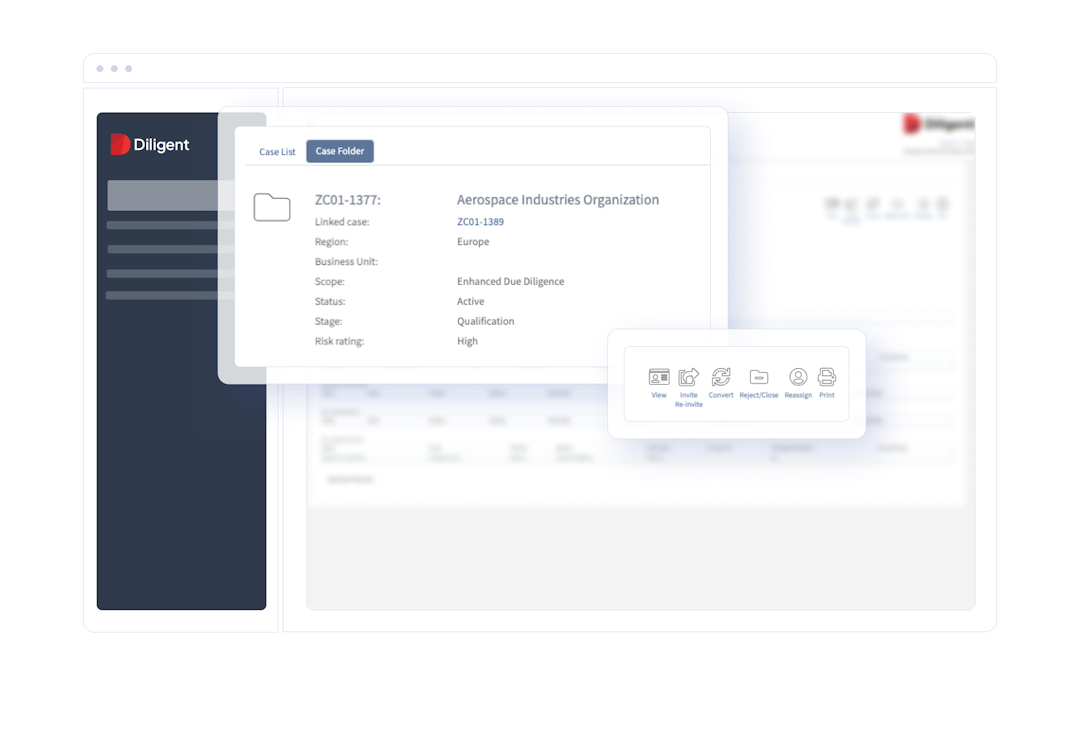
Stay compliant and avoid penalties
Leverage Third-Party Manager’s advanced business intelligence platform to stay ahead of local and international regulations and minimize the risk of noncompliance fines.
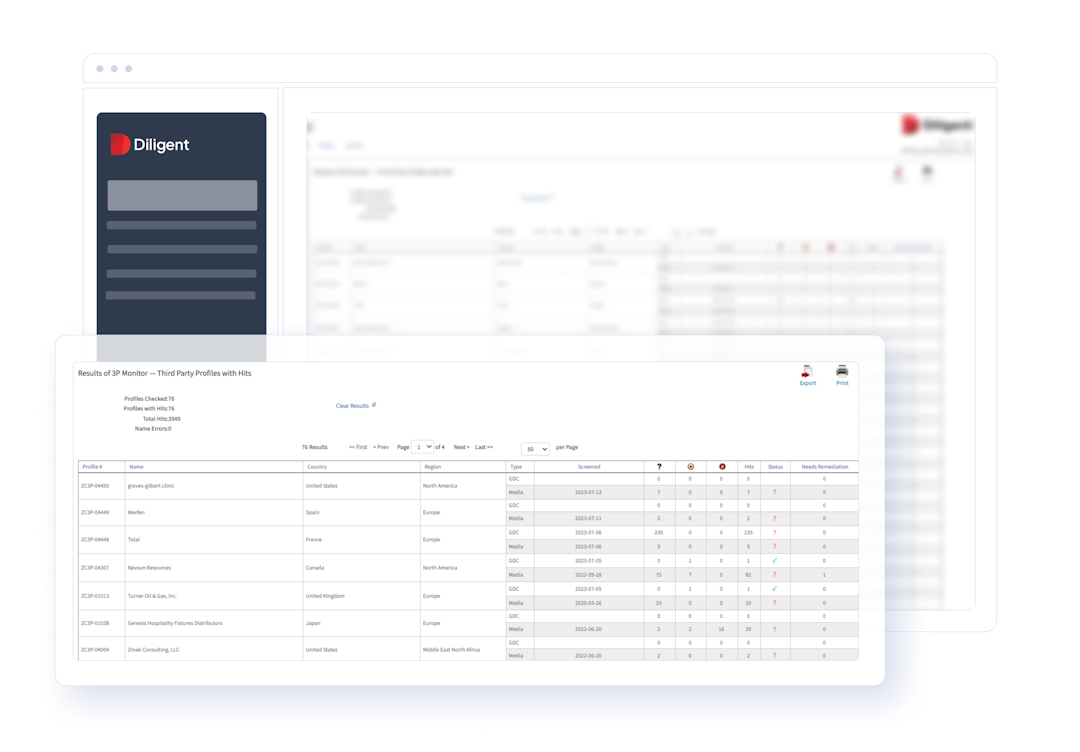
Make sharper decisions with comprehensive risk insights
Make informed decisions with a comprehensive view of third-party risks. Track risks in real time with in-depth analytics to get the full story on potential partners and improve decision making.
Kohler Co. automates third-party risk management with Diligent
Learn how Kohler Co. used Diligent to mitigate risks, track compliance and streamline its risk management process, consolidating its third-party risk management tools in a single platform.

Strengthen business relationships and build trust
Cultivate stronger, more transparent partnerships with your third parties. Build a reputation for integrity on rigorous due diligence, real-time insights and continuous monitoring.

Apply multiple risk models across your engagements
Get comprehensive visibility into risk distribution and trends with aconfigurable risk engine that creates custom riskmodels, assigns assessment workflows and scopesbased on risk level.
A unified GRC platform that consolidates risk across your organization
Set up your leadersfor greater success with the Diligent One Platform. Give directors a consolidated view of risk across your entire organization. Empower better collaboration across governance, audit, risk and compliance by providing real-time intelligence. Accelerate action — while eliminating the need for multiple vendors.
Whether you’re moving off spreadsheets for the first time or optimizing your program, the Diligent One Platform scales to meet your needs.
Let’s talk.
Does your organization practice best-in-class governance?
Schedule a no-risk demo to see why 700,000 directors trust Diligent to elevate their governance practices.
Let’s talk.
Happy Diligent customer
“It was clear that our [third-party due diligence] process was taking too long. So, we needed to understand where the major delays were and how we could make this process easier for our stakeholders. After implementing Third-Party Manager we have reduced third-party due diligence processing time by 25% within six months."
Brian Risser, Business Partner Program Manager, TE Connectivity
We are committed to providing a robust and secure service that protects all our customers’ data.
Diligent’s Security Program is governed based on the NIST Cybersecurity Framework and Diligent follows ISO/IEC 27001 standards to keep information assets secure by implementing an Information Security Management System (ISMS).





