Protect your digital assets with IT Risk Management
Cyberattacks on your networks are relentless. Mitigate risks such as ransomware and data loss with proactive tools that identify, assess and remediate risks. Automate your cybersecurity program and provide the C-suite and the board with actionable insights.


Mitigate cyber risk
Improve your cybersecurity effectiveness by shifting from a reactive risk program to a proactive, forward-thinking approach.
Deliver real-time visibility
Boards and senior leaders need a deeper understanding of your IT risk posture. Give them the actionable insights they need.
Reduce risk management costs
Save money by automating repetitive manual tasks and streamlining data analytics. Free your team to focus on more strategic initiatives.
Clarify your risk posture
Cybercriminals prey on gaps in your security. Close those gaps and unify your program with one unified platform.
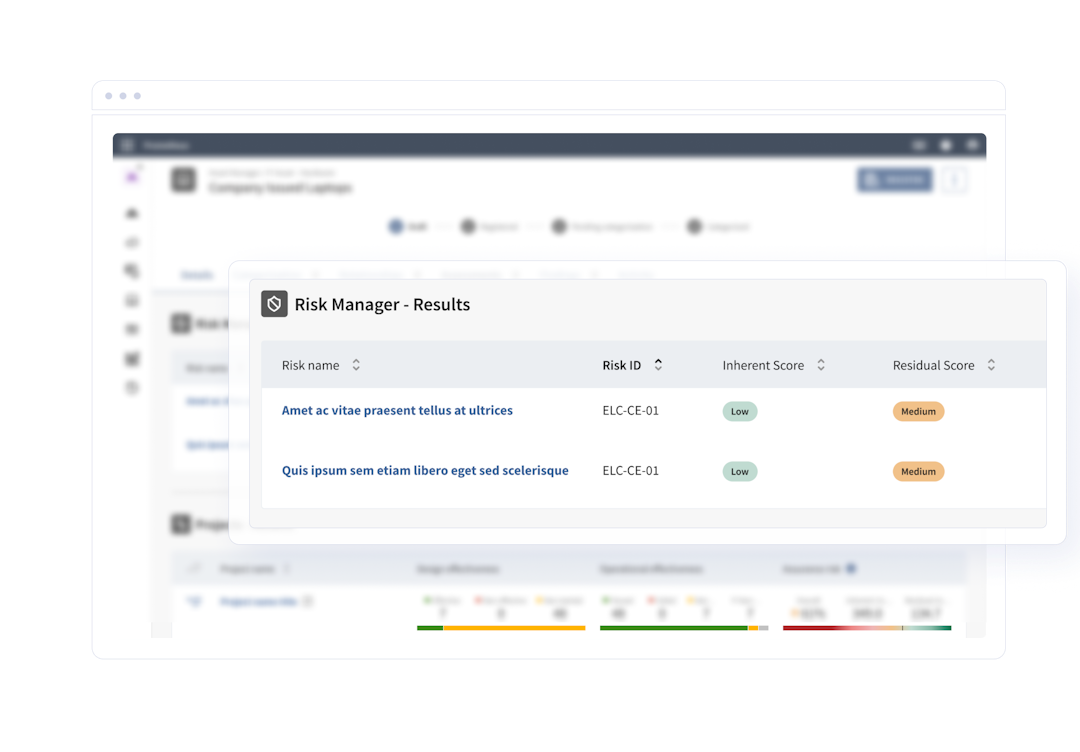
Anticipate & mitigate threats
Hackers continually invest in new technologies and methodologies. Our platform empowers you to guard against current and evolving hacker strategies. Our solution also integrates with existing tools and enhances their effectiveness.
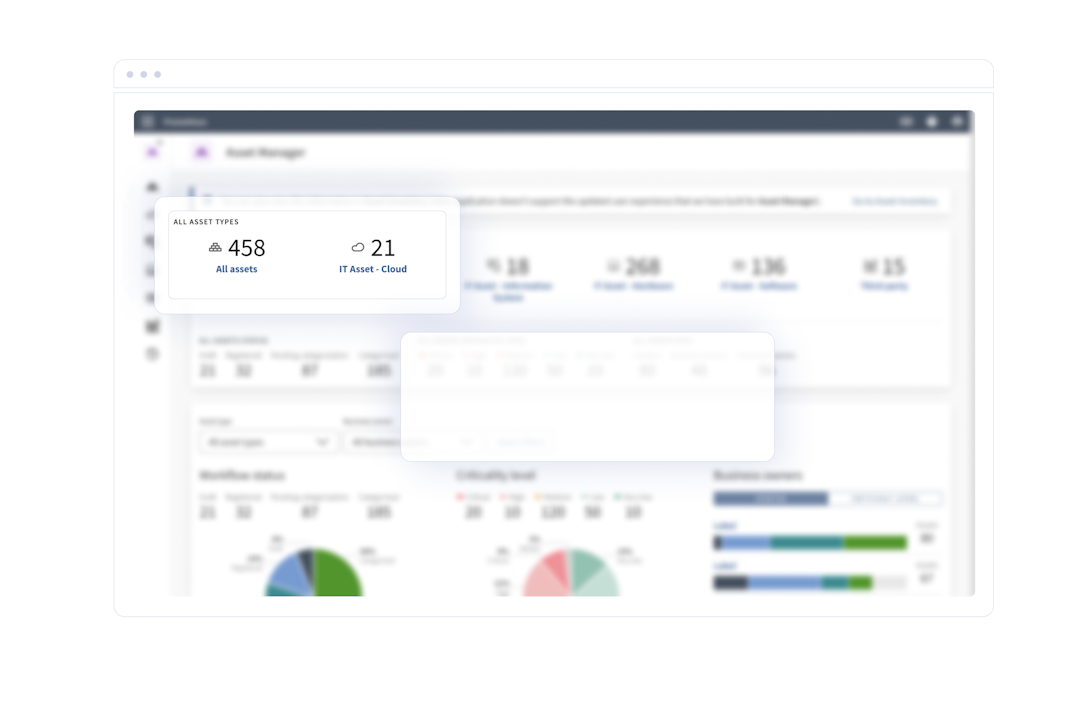
C-suite and board visibility
Cybersecurity and operational resilience are core boardroom topics now. Give leaders the visibility they expect — and wow them with insights that broaden their knowledge. Also, equip your security teams with intuitive dashboards for predictive, preventive and responsive strategies.
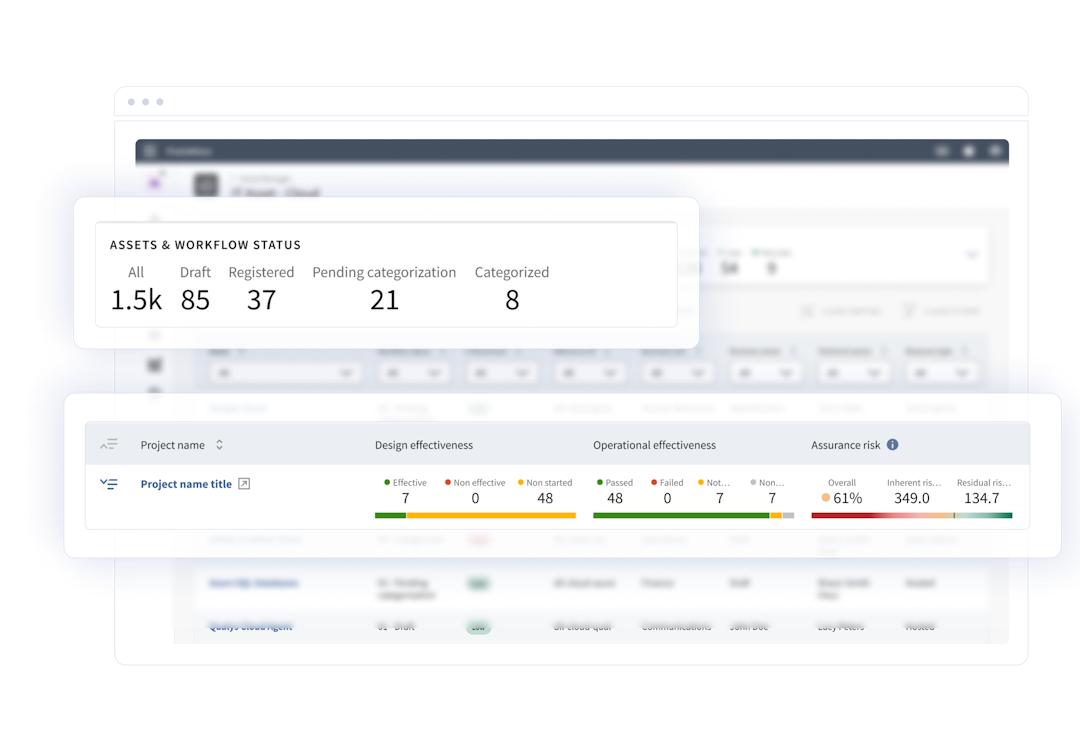
Save money, reduce risk
Don’t waste time or money building homegrown IT risk workflows. Our prebuilt IT risk workflows reflect best practices from thousands of engagements. Let your team focus on the strategies to reduce risk and cost.
MCS streamlines and improves its risk management
By using Diligent, MCS has greatly improved the efficacy of its risk management. “Through Diligent, we’ve been able to identify areas of weakness, where we need to shore up our risk management, and we’ve also been able to elevate information up to our boards,” said Wade.

Expert support, seamless integration
Unmatched support around the clock
Understanding that board responsibilities can call for immediate action at any time, we ensure that our support is available 24/7/365.
Effortless onboarding and seamless transition
Whether you're new to Risk Management software or moving from another solution, our dedicated onboarding and implementation experts are here to make the process run smoothly.
Tailored training programs
Enhance your skills alongside your peers in our live, instructor-led training sessions designed for both new and seasoned users.
See why 50% of the Fortune 1000 trust Diligent
Get your personalized demo today.
See firsthand how the world’s leading IT Risk Management software scales to your organization’s needs.
We are committed to providing a robust and secure service that protects all our customers’ data.
Diligent’s Security Program is governed based on the NIST Cybersecurity Framework and Diligent follows ISO/IEC 27001 standards to keep information assets secure by implementing an Information Security Management System (ISMS).






