Diligent One Platform Trust and Compliance
Secure by design.
Diligent One Platform is a Software-as-a-Service (SaaS) platform that offers a unified solution designed to revolutionize the way boards, committees, and executives navigate risk.
Benefits of the Platform Approach to Security
Secure-by-design architecture based on the shared responsibility model.
- AWS is responsible for security of the cloud (global infrastructure).
- Diligent is responsible for security in the cloud (the SaaS platform).
- Customers are responsible for what goes in the cloud (your data, your users).
Global availability with regionalized data storage and protections to comply with data privacy and location requirements.
Supported regions include:
- United States (U.S. East – North Virginia)
- Canada (Canada – Central)
- Europe (Europe – Frankfurt)
- Europe (Europe - London)
- Asia Pacific (Asia Pacific – Tokyo)
- Asia Pacific (Asia Pacific – Singapore)
- Australia (Asia Pacific – Sydney)
- South America (Brazil)
- Africa (South Africa)
- U.S. Federal Customers (AWS GovCloud)
- U.S. State/Local/Education Customers (AWS GovCloud)
Unified governance and compliance across the platform.
Diligent’s Security Program is based on the NIST Cybersecurity Framework and Diligent follows ISO/IEC 27001 standards.
The platform is ISO 27001 certified and undergoes annual SSAE 18 SOC 2 Type II audits.
Security Organization
Diligent has a dedicated Security department comprising a diverse team of security professionals focusing on product security, security operations, incident response, risk management, and compliance.
The Security Team is led by Diligent’s Chief Information Security Officer (CISO).
The Shared Responsibility Model
Security and compliance is a shared responsibility between Diligent and its customers. Diligent manages the overall application infrastructure and customers manage the end-user security and access control to their individual system.
Customers should have controls in place to restrict access to the individuals for whom account access is required. Controls should include:
- approving individuals for access to accounts prior to setting up users in the system.
- revoking users’ log-in credentials when user access is no longer required or if user authentication credentials or other sensitive information has been compromised.

Amazon Web Services (AWS) Responsibility
Amazon is the largest vendor of data storage and computing on the planet, and they are responsible for the physical facility as well as the physical infrastructure of server hardware, networking, and related services for the Diligent One Platform and hosting customer data.
Diligent Responsibility
In addition to the physical and hardware security that Amazon provides, Diligent also has a robust information security environment to ensure that the confidentiality, integrity and availability of customer data meets high standards and customer expectations.
Customer Responsibility
Customers share the responsibility of not only keeping their data secure, but also complying with applicable regulatory or privacy laws.
- Customers have full ownership of their user access controls.
- Customers manage their entire data lifecycle.
- Customers decide what information goes into the system, how long it should be retained, and what data should be deleted.
- Customers determine who can access their data.
Platform Capabilities for Customer Responsibilities
The platform includes capabilities to assist customers in their responsibility for managing end-user system access:
- Enforce strong passwords
- Configure password expiry
- Configure session timeout
- Configure SSO (Single-Sign On) via SAML 2.0
- Challenge user accounts after multiple failed logins
- Easily delete or suspend user accounts
- Specifically identify permissible user IP addresses
- Use activity tracking to log access and system use
Regional Availability and Data Protections
Diligent One Platform is available in multiple regions to give customers options for where their data is stored, and to enable them to comply with data privacy location requirements.
Regional Data Storage
Data is stored and replicated across state-of-the-art data centers operated by Amazon Web Services (AWS). Upon system setup, your platform data is stored in the data center region associated with the address listed in your Order Form. You may choose an alternative storage region to suit your physical, legal, security, or performance needs.
Data is encrypted during transmission and at rest (AES-256) within the regional data storage facility. All platform customer data, including data in backups, are stored exclusively in the single hosting region.
Data and Service Redundancy
All regional equipment is fully redundant and data is replicated or backed-up to alternate regional locations in case of failure.
In addition to this real-time redundancy, we back up all customer data, including field data and attached documents that are stored in your account within the system. A full backup of the entire system database is run daily and retained for a one-year period.
Backups are kept for the purpose of restoring data integrity due to systemic or database failure, but not for the purpose of restoring user deleted data. As long as your subscription is active, your data will be backed up.
Data ownership
Customers own their data completely and are responsible for setting retention spans and for deleting unwanted content during the subscribed service and up to 30 days after termination or expiry of their subscription. Customers have a responsibility of ensuring their data is compliant with applicable policies, regulations, and laws. Diligent has the responsibility of ensuring the platform hosting customer data is secure.
Customers have several ways (authorized managers or administrators) to extract data at any time.
Terminating subscriptions
When you choose to terminate your subscription, Diligent will extend access to the system for an additional 30 days to copy or extract any data you wish to retain. Once you have extracted your data, you have the full ability and responsibility to delete any or all your remaining data in the system.
Upon written request, Diligent will destroy the customer system and all data content after the extract process. If 90 days has passed without written request to destroy the customer system, Diligent reserves the right to destroy the customer system to regain system resources. For product specific terms, see https://www.diligent.com/governance-cloud-terms-conditions/
Service Resiliency
Diligent is committed to delivering a world-class customer experience. Engineering teams actively monitor the platform for availability and performance to a 99.5%+ average uptime. To access current system status page please visit: https://status.diligent.com.
Diligent maintains a disaster recovery plan. While the customer impact of a physical or environmental threat to its corporate headquarters is considered low (since the vast majority of internal tooling is cloud-based), Diligent personnel's safety and availability is mission critical.
The maximum acceptable length of data loss for the platform (recovery point objective or RPO) is one hour, even in the event of disaster. Therefore, backup intervals are configured to allow for loss of customer data of one hour or less, depending on the time of system failure.
The targeted duration of time and a service level within which service must be restored after a disaster (recovery time objective or RTO) is currently 24 hours.
Data Privacy
Customer data is considered confidential information and is handled securely by Diligent personnel. Customer data is never copied to assets outside the production environment, including employee laptops.
Any troubleshooting that needs to be performed on customer data is performed in the customer’s environment. When Diligent personnel need access to a customer environment, a ticket is generated indicating that Support accessed the instance, why the interaction was necessary, and what work was performed.
Actions by Diligent personnel on a customer’s system are limited to resolving the customer needs, and nothing more. Once a customer is satisfied with the result, and the ticket is closed, access is removed. Diligent collects only the minimum personally identifiable information necessary from your licensed users for purposes of account set-up, access to product resources, and system administration.
Compliance
Platform Compliance
Diligent follows ISO/IEC 27001 standards to keep information assets secure by implementing an Information Security Management System (ISMS). This provides a systematic approach for managing risk across Diligent’s staff, processes, and IT systems. Diligent's ISMS is ISO/IEC 27001:2013 certified.
Diligent One Platform undergoes annual SSAE 18 SOC 2 Type II audits. The SOC 2 Type II audit is an industry recognized, independent audit, which reports on the suitability of the design, and operating effectiveness of Diligent’s controls relating to security, availability, and confidentiality.
Hosting Provider Compliance (AWS)
Amazon is the largest vendor of data storage and computing on the planet, and they are responsible for the physical facility as well as the physical infrastructure of server hardware, networking, and related services for the Diligent One Platform service and hosting customer data.
These controls ensure facility and equipment safeguards for areas such as multi-factor access controls, electronic surveillance, intrusion detection systems and environmental safeguards.
For more information about Amazon Web Services security, refer to the following documents:
- AWS Artifact (SOC 2, ISO compliance reports)
- AWS Cloud Security (overview on AWS security)
- AWS Compliance Roadmap (list of AWS security compliance programs)
If you would like to obtain any of the AWS compliance reports, especially their SOC 2, please request instructions from your Diligent account executive. Based on the standard agreement all SaaS vendors have with Amazon, Diligent cannot provide these reports directly to you. However, your account executive will help you with information to how to obtain reports directly from Amazon.
Reviewing Diligent Policies, Security Documentation, and Audit Reports
Robust information security policies and processes are the foundation of Diligent One Platform’s security program. Security is reinforced by a range of operational and security policies, standards, and procedures that address various controls and requirements. These measures ensure that our customers can trust the platform to protect their data and maintain the highest levels of confidentiality, integrity, and availability.
Upon request and subject to a standard non-disclosure agreement (NDA), customers can obtain a copy of the current platform SOC 2 report. A detailed list of policies is also available upon request.
Visit the document portal at trust.diligent.com for self-serve access to the following:
- Security policies and standards.
- Additional security documentation for the platform and specific modules.
- Third-party audit reports such as SOC 2 and HIPAA, ISO certifications, and penetration test reports.
Platform Security Controls
Diligent One Platform security is founded on the controls that are built into the service to protect customer data. Management regularly assesses risk, monitors the controls, evaluates potential threats, and uses this information to update the controls framework from policies and procedures to encryption protocols.
Data Encryption
Strong encryption is used to protect all data in transit and at rest.
Encryption in transit is achieved via the industry- standard TLS (Transport Layer Security) protocol supporting only the strongest encryption algorithms, including AES (Advanced Encryption Standard) with up to 256-bit key lengths. Encryption at rest is achieved by leveraging AWS storage encryption, using AWS KMS to create and store the 256-bit AES encryption keys.
By using TLS version 1.3, an encrypted communication channel between the end-user web browser and the platform is established, ensuring the confidentiality and integrity of all data transmissions from end-to-end.
The AES encryption algorithm is widely recognized and approved by organizations worldwide as an industry standard in government, military, and commercial applications.
All emails from our platform are transmitted via TLS-encrypted channels, when available.
Password Management
User passwords are never stored in clear text format. A strong cryptographic algorithm is used to generate irreversible strings known as password hashes. The algorithm also uses a unique long random value known as a salt, which is different for each user and ensures protection against attacks based on pre-computation of password hashes.
Password Attempts
When signing in to our platform or generating a token to use in another application, users have up to five attempts to enter your password. After five attempts, reCAPTCHA displays. reCAPTCHA is a service that protects websites from spam and abuse, and requires you to enter a series of characters or numbers to prove you are human.
Session expiry
A session is a period of activity between a user logging in and out of an application. Sessions are global to all platform modules. Your session expires if you are inactive for the duration of time set by an Account Admin.
Anti-malware Protections
Files uploaded to the platform are scanned for malware to protect users.
Event Monitoring
All product systems are monitored 24/7 for security and availability. In the event of any service interruption, alerts are delivered via e-mail, text message, and phone call to system administrators and management.
Security and performance are monitored using sophisticated third-party monitoring tools. Security and performance requirements are reviewed on a weekly basis and any issues noted that potentially impact customers are documented and resolved.
Privileged Access
Diligent follows the principle of least privilege for internal administration. Employees who require administrative access must be requested via a ticketing system. The request requires the approval from management before access is granted.
Diligent's administrative access is protected with a combination of network restrictions, username/password, multi-factor authentication, and private keys. Session limits for inactivity are set to 15 mins.
All access is tracked and monitored for suspicious activity. Administrative access to all applications is granted to employees only based on user job responsibilities. Access to all production system and internal applications is removed upon termination of employment.
Secure Software Development Life Cycle (SSDLC)
At all phases in the application development process, security is a top priority. Diligent builds security into the platform.
Secure coding best practices are strictly followed. Common application layer vulnerabilities, including all OWASP Top 10 vulnerabilities, are explicitly addressed at all stages of the SDLC using industry standard counter-measures, such as explicit sanitization of all user input, use of parameterized queries, and use of secure libraries. All code changes are controlled and approved, and must go through strict peer review and Quality Assurance (QA) testing prior to production deployment.
Segregation of duties
Procedures, controls, and monitoring are in place to ensure that a separation of duties exist between the define, design, build, test, and deploy phases of the software lifecycle. Third-party monitoring tools are used for development, test, and production to detect run-time errors and monitor performance so multiple stakeholders are informed on deploy or error.
Penetration testing
In addition to internal security testing, Diligent uses 3rd party independent penetration testing to check for security vulnerabilities. These tests are performed by an organization specializing in software security, and are used to probe the environment for vulnerabilities, such as cross-site scripting, SQL Injection, session and cookie management. Exploitable vulnerabilities are resolved in a timely basis based on severity and impact. A copy of the most recent penetration test report can be provided, subject to a non-disclosure agreement (NDA).
Web scans and testing
Platform source code is maintained in a repository exclusively for source code management. The source code repository is a complete copy of the source code. Vulnerability scans are performed to identify security flaws within the source code and dynamically on all applications prior to a production release. Any findings are resolved in a timely fashion.
Incident Management
Diligent has a robust platform Incident Response Plan to promptly and effectively manage incidents that minimize impact to the platform.
There is a Security Incident Response Team (SIRT) that is responsible for responding, managing, and conducting security investigations, including all aspects of communication such as deciding how, when, and to whom the findings shall be reported.
Incident Response Plan
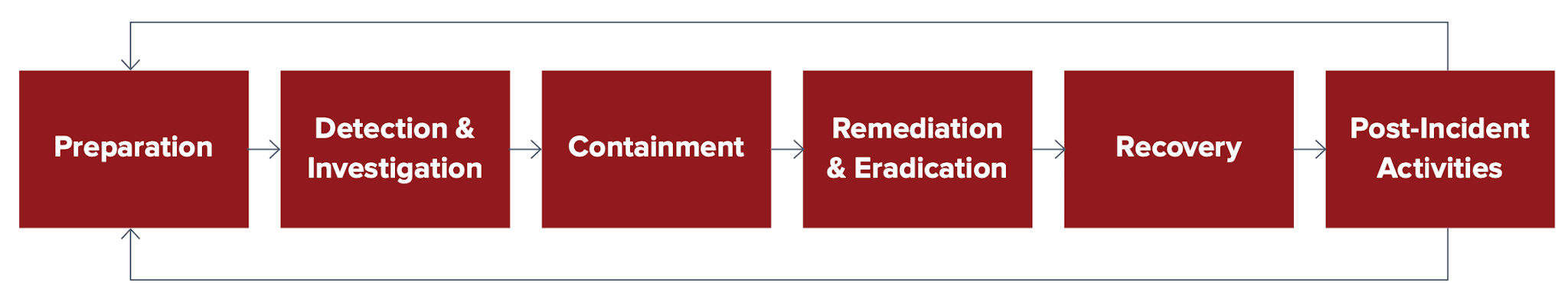
- Preparation - activities that enable the SIRT to respond to an incident: policies, tools, procedures, training, effective governance, and communication plans.
Preparation also implies that the affected groups have instituted the controls necessary to recover and continue operations after an incident is discovered. Post-mortem analyses from prior incidents form the basis for continuous improvement of this stage. - Detection & Investigation - the discovery of the event with security tools or notification by an inside or outside party about a suspected incident and the declaration and initial classification of the incident. Investigation includes completing an Incident Log to keep track of all incident activities.
Diligent monitors and investigate all events and reports of suspicious or unexpected activity, and tracks them in an internal ticketing system. Investigation is the phase where SIRT personnel identify and determine the priority, scope, and root cause of the incident. - Containment - the triage phase where the affected host or system is identified, isolated or otherwise mitigated, and when affected parties are notified and investigative status established.
This phase includes sub-procedures for seizure and evidence handling, escalation, and communication. All evidence will be handled in accordance with local evidence handling procedures and legal requirements. - Remediation & Eradication - the post-incident repair and recovery of affected systems and or data, communication and instruction to affected parties, and analysis that confirms the threat has been contained.
Apart from any formal reports, the post-mortem will be completed at this stage as it may impact the remediation and interpretation of the incident. - Recovery - the analysis of the incident for its procedural and policy implications, the gathering of metrics, and the incorporation of “lessons learned” into future response activities and training.
- Post-incident Activities - activities within the recovery stage include “Lessons Learned.” Lessons Learned allows the SIRT to identify any weaknesses in the plan and the supporting policy and or process and to put in place remedial actions to mitigate any further such incident.
During lesson learned, the SIRT will review the incident and examine all associated artefacts to identify any root cause. Lessons learned are documented and used to improve the plan.
Diligent Generative AI Usage Principles
AI Safety and Ethics Task Force
Diligent is committed to responsible AI deployment. Diligent maintains an AI Safety and Ethics task force comprised of Information Security, Legal, Product, Engineering, and Executive Leadership. This task force meets regularly to actively ensure our use of AI technologies meets the highest ethical and safety standards.
Diligent Generative AI Principles
By default, Diligent does not use AI models trained on data belonging to customers. Any deviation from this principle requires customer authorization and is always the customer’s choice. Furthermore, Diligent products label AI generated content to assist users with identifying AI-generated information.
Diligent develops AI functionality following the same secure development process as non-AI functionality. Information security controls that protect customer data (e.g. retention, encryption, and residency) are maintained at the same level. Diligent products use Amazon Bedrock for hosting and running AI models. For more details, see Data protection - Amazon Bedrock